Tag: vulnerability
Showing 3 posts
-
Poster 2025.11.02
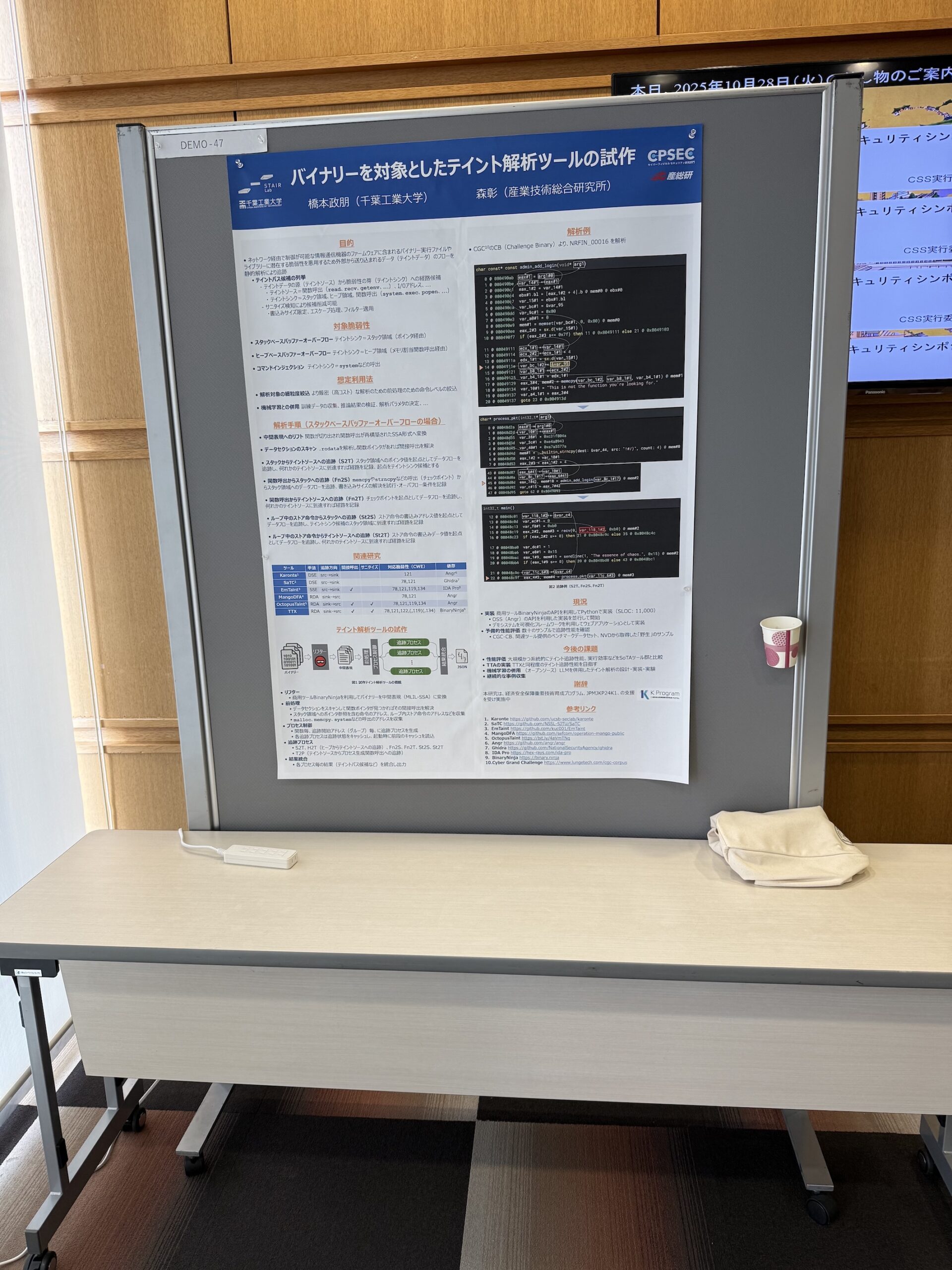
Poster 2025.11.02
バイナリーを対象としたテイント解析ツールの試作(CSS2025) An Implementation of Static Taint Analysis for Binaries
先日、岡山コンベンションセンターにて開催されたコンピュータセキュリティシンポジウムにて研究成果のデモンストレーション(ポスター発表)を行いました。 デモンストレーションセッションはシンポジウム初日と2日目に実施されました... -
Publications 2022.01.19
Publications 2022.01.19
脆弱性自動検知に向けたバイナリプログラム解析ツールの開発(SCIS2022) Development of a Binary Program Analysis Tool for Automatic Vulnerability Detection
泉田大宗(IIJ技術研究所), 橋本政朋(千葉工業大学), 森彰(産業技術総合研究所) 2022年暗号と情報セキュリティシンポジウム 筆者らは、IoTデバイスのセキュリティを自動的に分析・診断する手法として、ファームウェ... -
Publications 2021.01.22
Publications 2021.01.22
脆弱性解析を用いた効果的なバイナリCFIの実現に向けて(SCIS2021) Toward Effective Enforcement of Binary-CFI with Vulnerability Analysis
橋本政朋(千葉工業大学)、泉田大宗(IIJイノベーションインスティテュート)、森彰(産業技術総合研究所) 2021年暗号と情報セキュリティシンポジウム CFI(control-flow integrity)とは,制御フロ...